SLAM Method: A Simple Method to Spot Phishing Emails
By far the most common reason for data breaches is because of human error. In 2022 Stanford University and Tessian (a security firm) led a study, “Psychology of Human Error”). The study revealed 88% of all data breaches occur because of human error. Distraction is the reason for victims falling for a phishing scam by 45% of affected individuals.
This study suggests that companies can significantly reduce their risk of cyberattacks with employee training.
The SLAM Method
We use a technique cyber security experts use to help employees minimize employees falling for a phishing scam. It’s called the SLAM method:
S- Sender
L- Link
A- Attachment
M- Message
S- Sender
One common cyber-criminal tactic is to mimic legitimate senders. While some scammers use obvious fake email addresses, more sophisticated criminals disguise their email addresses to resemble valid ones. These email addresses intentionally mislead individuals who aren’t paying attention. For example, email address might have two n’s versus a “m”.
One of the findings of the “Psychology of Human Error” study suggests that 43% of people click on scam emails because they believe the email is legitimate. The possibility of falling victim to these email scams increases if the email appears to be from a senior executive within the company or from a recognized branded company.
Below is an example of a phishing email. The email address for the sender is not legitimate as it comes from a Gmail account and is not a work email. At first glance, the email below appears to be work-related. However, it is from a personal account versus a company email address.
If an email seems that it might be legitimate, instead of acting on it, go directly to the sender. Contact the sender through a known good phone number (not a number from the email), or find the information from a trusted source. Employees should always confirm the email is legitimate before taking any requested action.
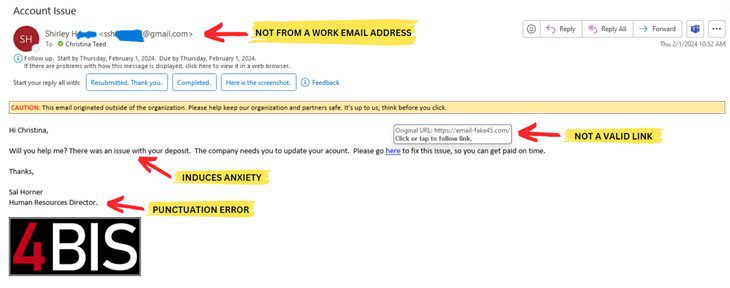
L- Link
Sending malicious links is one attempt cyber-criminals use to install codes to infiltrate a system. Before clicking on a link, everyone should hover over the link (DO NOT CLICK ON LINK) to see where the URL leads. Verify the link is going to a good location. If you are not expecting a link then don’t click on it. Go to the companies website directly to find the information if you are unsure the link is valid. Do not enter your login information after clicking on a link you are not 100% sure of its legitimacy.
A- Attachments
Another attempt cyber-criminals use to send malicious code is installing code from attachments. The National Cybersecurity Alliance states it best, “If you click on a phishing link or file, you can hand over your personal information to the cyber-criminals”.
Here at 4BIS Cyber Security we use software to safeguard computers and networks against the installation of harmful code. The software blocks unfamiliar software or attachments that come from unfamiliar sources. The software also allows us as IT providers to limit access to the PC and network.
However, even with great software such as what we use, nothing can make it 100% a perfect defense. This is why the best defense is a combination of software and diligence.
M- Message Text
To avoid falling victim, employees should scrutinize emails for red flags such as spelling or grammar mistakes, urgent requests (i.e., a late-night message from the CEO asking you to buy gift cards), or emails sent at odd hours. These could indicate that the email is a scam.
Or the opposite can be true. Are they making an offer that sounds too good?
When you receive a message, consider how urgent it feels. Does the email provoke fear or anxiety? Criminals try to incite these reactions, so people act impulsively. If the email stirs up emotions, examine the entire message carefully before responding.
What if I fall victim to a phishing scam?
Once you have identified spam, mark it as spam or junk. Do not forward the email to anyone. We highly suggest contacting your IT department to place the sender on a blocklist.
If you do click on a link from a phishing email or reply to an email scam. Notifying your IT company should be the first step to minimize any potential harm. At a minimum, your computer should be scanned for any harmful software that may have been installed.
Your IT provider will have an immediate response time, examine potential risks and minimize work disruptions. Additionally, your IT provider will work to keep business operations running smoothly.
Great IT providers offer or require training options for employees. We require all employees to take part in ongoing active and hands-on training courses. The goal is to use education as a preventive tool.
This training includes emails mimicking what cyber-criminals send out. If an employee replies to the email or clicks on a link, the training system will email the recipient with notes. The software also notifies your IT company.
Having an experienced and qualified MSP (Managed Service Provider) taking care of your company data gives peace of mind. At 4BIS Cyber Security, we have thirty years of experience. We love knowing we are keeping our client’s data secure and their employees working!
Contact us to discuss what strategies and training would work best for your company!
