EasyPark data breach: A lesson in good breach notification.
EasyPark, one of the largest parking app operators in Europe, suffered a data breach. According to the breach page on the EasyPark website the attackers stole some customer data but did not impact service. There are not a lot of details on the how of the breach happened but there is good information that is important to the people affected. Let’s take a look at why this is a good example of breach notification.
Disclaimer
Your company’s incident response plan should be built in collaboration with your legal, cyber insurance, and cyber security teams. This article is not legal advice but designed to be educational on what good incident reporting can look like. We at 4BIS Cyber Security do not have any information about the EasyPark breach than what is publicly available.
Notification to Effected Parties
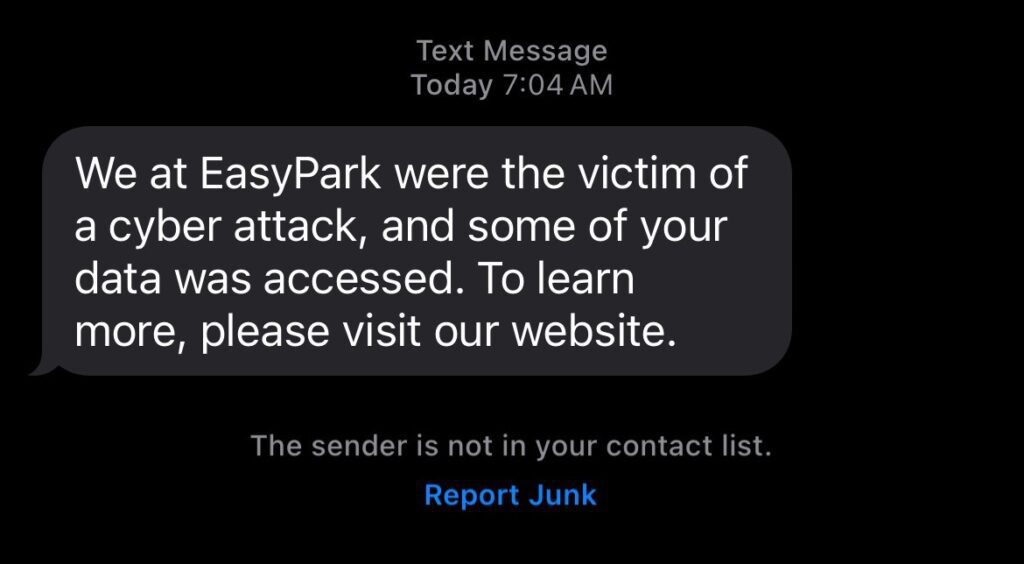
EasyPark sent out a text message to people affected by the breach. The message said the following.
“We at EasyPark were the victim of a cyber attack, and some of your data was accessed. To learn more, please visit our website.”
There were a few things I really liked about this method.
There were no links and a simple call to action.
EasyPark could have very easily put a link to their website, or some other source for the breach data. The fact that they did not should be the standard in the industry. Not having a link requires more work for the end user but it built trust. The simple call to action to go to the EasyPark website for more information had the correct tone. Someone running a phishing campaign would have had a link with a more urgent call to action.
The message was clear on what happened.
We were the victim of a cyber attack, and some of your data was accessed. It let people know the situation required their attention.
The message was short.
At 24 words it got the message through quickly.
EasyPark Data Breach webpage
Once you got to the EasyPark webpage there is a banner at the top pointing you to the breach page. They were open that it happened and we not trying to hide it.
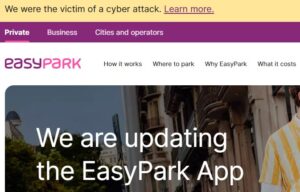
The breach page was simple to follow and conveyed the information most important to the people affected. The page is broken into 4 parts:
1. We took actions to protect you.
Quickly convey that they stopped the breach, contacted the authorities, and are working to make sure it doesn’t happen again.
2. We are making you aware.
If you received a message you were affected. They then listed exactly the data that was accessed. Very importantly there was a call to action to be mindful of phishing attempts. The information gathered will be used to scam people out of money.
3. We are sorry.
EasyPark apologized that this happened and they are working to prevent this in the future.
4. FAQ section.
The most important information to most people was contained in the 3 previous sections. The FAQ contains more information but the critical data was presented in a clear, concise manner.
What can we learn from this?
EasyPark seems to know exactly what happened and what data was accessed. This can only be done through the correct logging of their systems. After an event happens you need to know what was accessed, who accessed it, how long was it accessed, and have the holes been patched that allowed the access. Facts matter and if you do not have the data you can not tell the facts.
Be honest and upfront.
Cyber attacks are not going away. Admit that you have had an incident and work to rectify the situation. Honest communication will gain you trust.
Moving forward.
Work with your Cyber Security company, cyber insurance provider, and legal team before a cyber event happens. Come up with an incident response plan that includes notification to affected parties/press. Hopefully you will never need these documents, but you do not want to be coming up with them if the worst happens.
4BIS Cyber Security offers cyber security risk assessments to show where you are vulnerable to attack. This is a wholistic overview of your company designed to find where you carry the most cyber risk. Please reach out for more information.